Krishna Radhakeesoon
The SWIFT Customer Security Programme (CSP) initiative was launched by the Society for Worldwide Interbank Financial Telecommunication (SWIFT) in 2016 and aims to strengthen the security of the global financial community.
The programme aims to bolster the security by setting out a series of mandatory and advisory security controls. These controls are designed to help SWIFT users enhance their cyber defenses and protect their SWIFT-related infrastructure.
As BDO is a Certified CSP Assessment Provider, we would like to share our insights into Swift’s focus areas for v2024 and the upcoming changes.
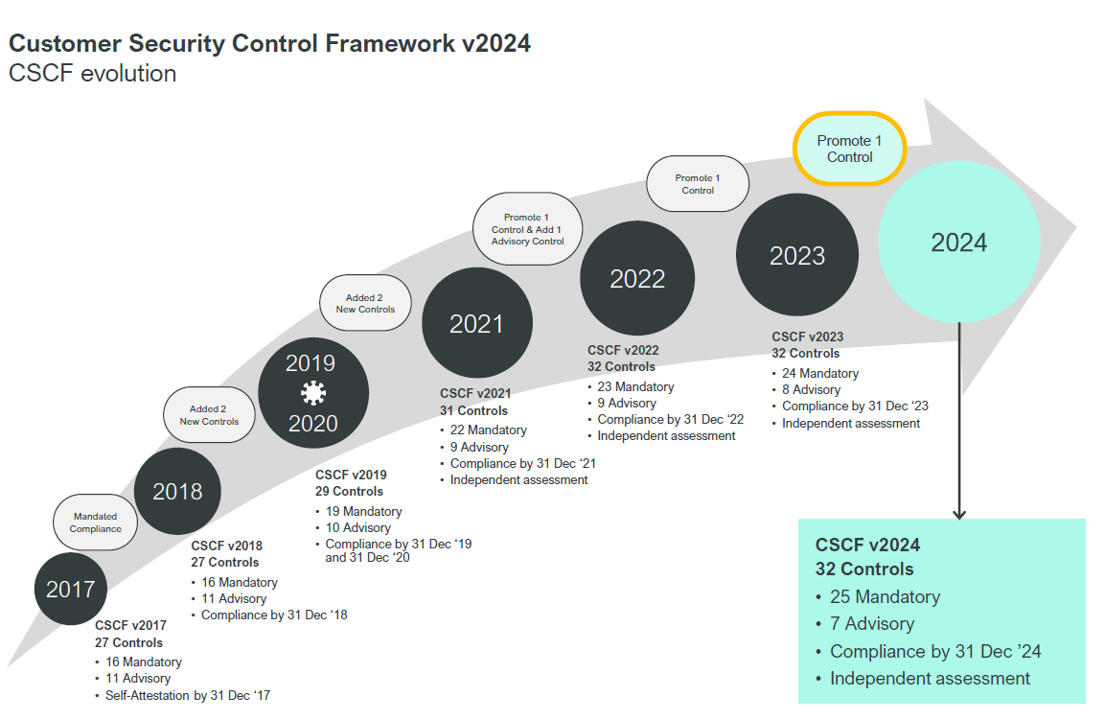
Swift has defined a set of security objectives, which are linked to seven principles and covered by the set of controls in the Customer Security Controls Framework (CSCF). The CSCF consists of 25 mandatory and 7 advisory controls, but not all controls are applicable to all architecture types: it depends on the extent to which an organisation is integrated with Swift systems.
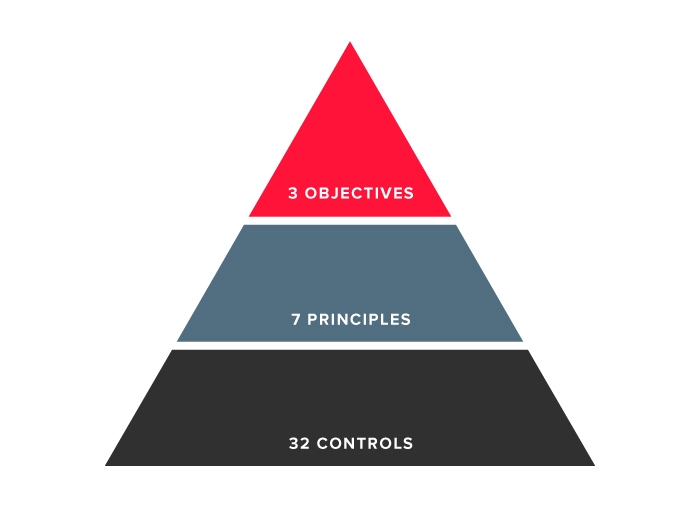 3 OBJECTIVES AND 7 PRINCIPLES:
3 OBJECTIVES AND 7 PRINCIPLES:1. Restrict Internet access & segregate critical systems from general IT environment
2. Reduce attack surface and vulnerabilities
3. Physically secure the environment
4. Prevent compromise of credentials
5. Manage identities and segregate privileges
6. Detect anomalous activity to system or transaction records
7. Plan for incident response and information sharing